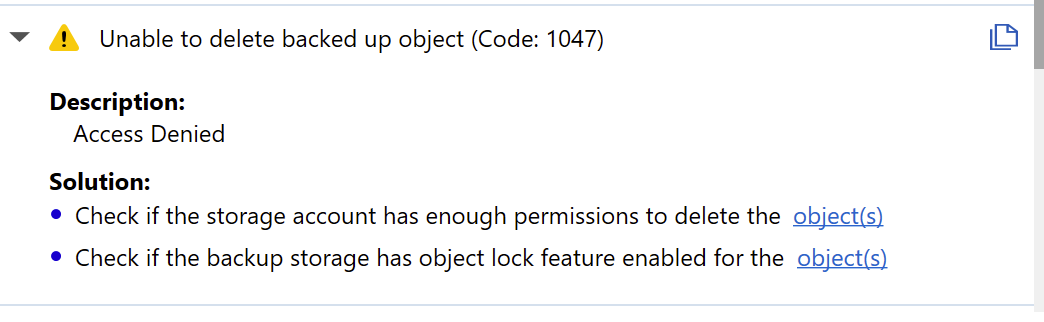
Unable to Delete Backed up Object (code 1047)
Situation
A backup plan terminates with the following warning: Unable to Delete Backed up Object.... Solutions contains links to backed up objects that cannot be deleted.
Cause
The occurrence of this warning generally means that the deletion of the object(s) is denied due to object lock feature enabled on the backup storage or that account specified for this backup storage has no enough permissions required for object deletion.
Solutions
- Solution 1. Check if the storage account has enough permissions to delete the object(s) on the management console of the backup storage. Use the link in the warning message to view the objects that were not deleted.
- Solution 2. Check if the backup storage has default object lock feature enabled for the object(s) on the management console of the backup storage.
- Solution 3. Check if the bucket policy, group policy, or user policy, if applicable, allows deletion or all operations and deletion is not denied. Should not contain allow permission for delete and do not contain deny
- Solution 4. Connection errors. Check if your backup storage is accessible.
Solution 1
Check the permissions of the account you use for the backup storage on the management console of the backup storage. For our product to work, DELETE operation permissions should be enabled for backup storage account. FullAccess ensure that delete operations are allowed, but in case you want more granular permissions, you should include all S3 operations for upload/delete/sync and STS Get* operations to be able generating temporary credentials. For example, WasabiWriteOnlyAccess allows write operations but NOT delete operations, and will result in this issue. You should change this to WasabiFullAccess to avoid the issue.
Solution 2
Check whether any Object Lock or Immutability features are enabled for the backup storage destination on the management console of the backup storage. These features prevent object deletion. You can change this object locking policy or change your retention policy according to it in case this policy is applied intentionally. The possibility to change the policy depend on how the Object Lock was enabled.
AWS S3
The settings that can be changed and saved:
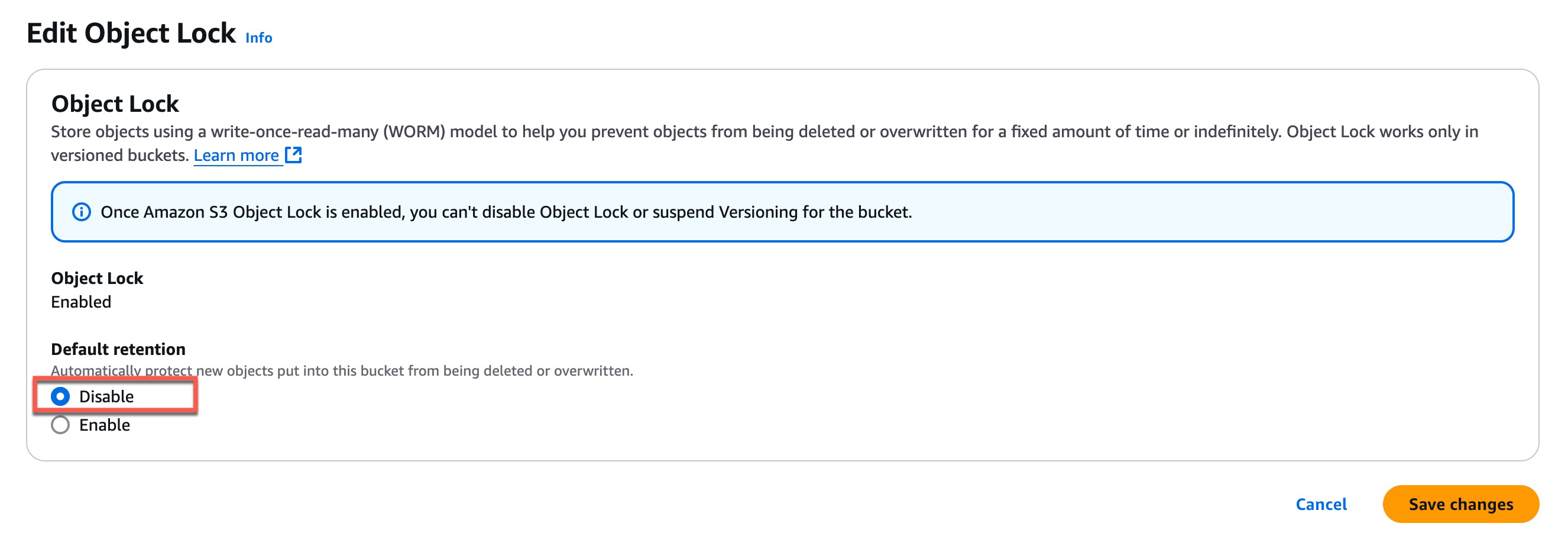
The changes are not supported and cannot be changed, because the Default Retention was enabled manually on the management console of the backup storage:

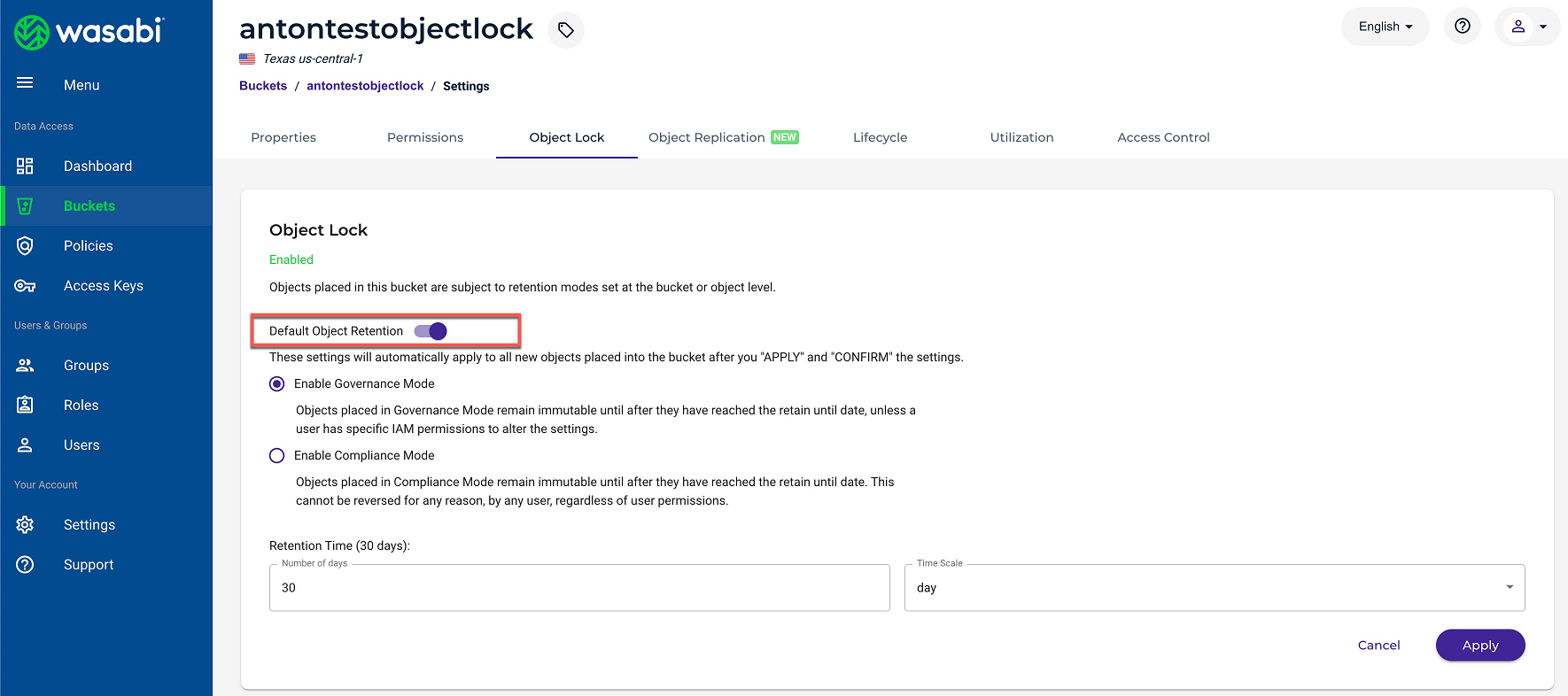
Wasabi
The settings that can be changed and saved:
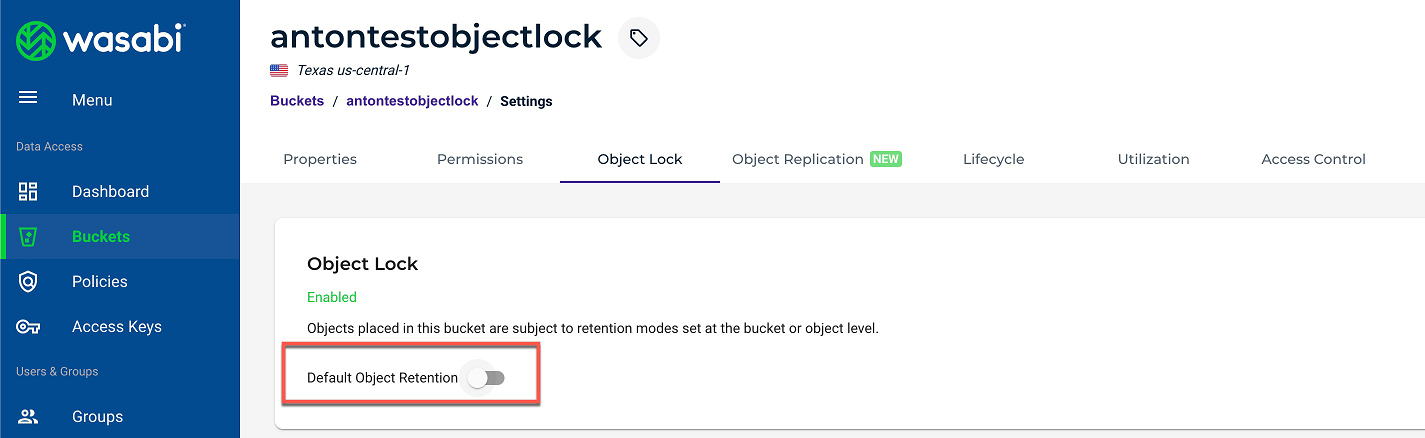
The changes are not supported and cannot be changed, because the Default Retention was enabled manually on the management console of the backup storage:
BackBlaze
The settings that can be changed and saved:
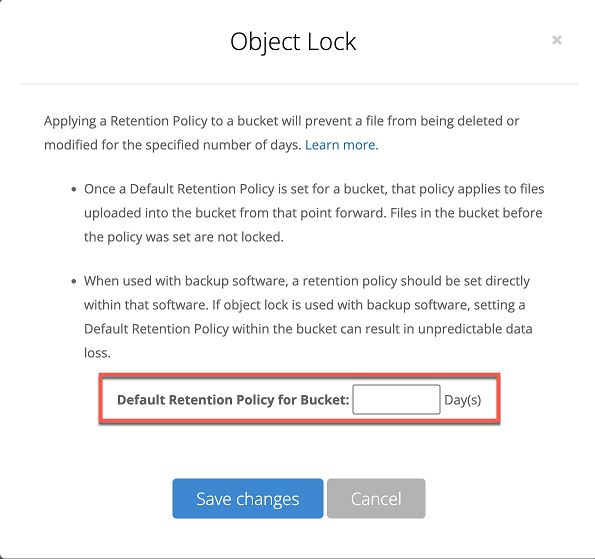
The changes are not supported and cannot be changed, because the Default Retention was enabled manually on the management console of the backup storage:
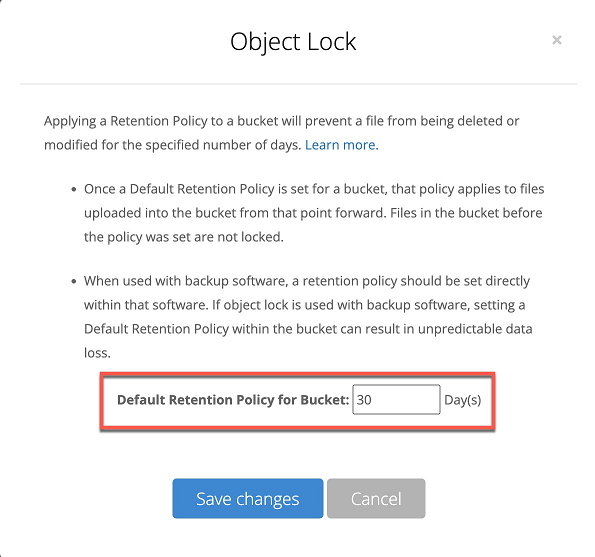
Solution 3
Open the management console of the backup storage. Check if the bucket policy, group policy, or user policy, if applicable, allows deletion or all operations and deletion is not denied.
AWS s3
The following policy statement allows all required operations:
{
"Statement": [
{
"Sid": "Statement1",
"Effect": "Allow",
"Action": [
"s3:*"
],
"Resource": []
}
]
}
Wasabi
The following user policy statement allows all required operations:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetBucketLocation",
"s3:GetBucketVersioning",
"s3:ListBucketMultipartUploads",
"s3:ListBucketVersions",
"s3:DeleteObject",
"s3:DeleteObjectVersion",
"s3:GetBucketObjectLockConfiguration",
"s3:PutBucketObjectLockConfiguration"
],
"Resource": "arn:aws:s3:::mybucket"
},
{
"Effect": "Allow",
"Action": [
"s3:AbortMultipartUpload",
"s3:ListMultipartUploadParts",
"s3:DeleteObject",
"s3:DeleteObjectVersion",
"s3:GetObject",
"s3:GetObjectVersion",
"s3:PutObject",
"s3:PutObjectRetention"
],
"Resource": "arn:aws:s3:::mybucket/*"
},
{
"Effect": "Allow",
"Action": "s3:ListAllMyBuckets",
"Resource": "*"
}
]
}
In case you see that the deletion operations are not allowed or denied you should correct the policies to avoid the issues.