EC2 restore error: The service role vmimport does not exist or does not have sufficient permissions for the service to continue
Situation
An image-based or VM restore plan to Amazon EC2 platform fails with the following error message: The service role vmimport does not exist or does not have sufficient permissions for the service to continue
Cause
Absence of the IAM service role and / or certain permissions necessary to import an image-based or VM backup as an EC2 instance.
Solutions
If you have encountered issues related to the vmimport IAM role during the EC2 restore of an image-based backup, consider the following troubleshooting strategies (starting with the first one):
- Check your current permissions;
- Set up the vmimport IAM role again;
- Re-add AWS S3 storage account to your [MSP portal] (https://mspbackups.com/AP/EditAccount.aspx) through the "IAM role (MBS wizard)" option.
1. Check your permissions
In order to restore your image-based backup as an EC2 instance, make sure that the following permissions are granted to your Amazon Web Services IAM role / user ([AWS management console] (console.aws.amazon.com) -> IAM -> Roles / Users -> Role name / User name -> Permissions)
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Action": "s3:DeleteBucket",
"Resource": "*",
"Condition": {}
},
{
"Effect": "Allow",
"Action": "s3:*",
"Resource": "*",
"Condition": {}
},
{
"Effect": "Allow",
"Action": "iam:SimulatePrincipalPolicy",
"Resource": "*",
"Condition": {}
},
{
"Effect": "Allow",
"Action": "s3:ListAllMyBuckets",
"Resource": "*",
"Condition": {}
},
{
"Effect": "Allow",
"Action": "ses:*",
"Resource": "*",
"Condition": {}
},
{
"Effect": "Allow",
"Action": "sns:*",
"Resource": "*",
"Condition": {}
},
{
"Effect": "Allow",
"Action": [
"ec2:ImportInstance",
"ec2:ImportImage",
"ec2:DescribeInstances",
"ec2:MonitorInstances",
"ec2:RequestSpotInstances",
"ec2:RunInstances",
"ec2:StartInstances",
"ec2:TerminateInstances",
"ec2:ModifyInstanceAttribute",
"ec2:CreateTags",
"ec2:CancelImportTask",
"ec2:StartInstances",
"ec2:DescribeConversionTasks",
"ec2:DescribeImportImageTasks",
"ec2:ImportVolume",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSubnets",
"ec2:StopInstances",
"ec2:DescribeKeyPairs",
"ec2:DescribeImages",
"ec2:ImportSnapshot",
"ec2:DescribeImportSnapshotTasks",
"ec2:CreateVolume",
"ec2:CreateImage",
"ec2:DescribeVolumes",
"ec2:DescribeSnapshots",
"ec2:DeleteSnapshot",
"ec2:CreateSnapshot",
"ec2:AttachVolume",
"ec2:DeregisterImage",
"iam:ListRoles"
],
"Resource": "*",
"Condition": {}
}
]
}
If you are granted with [MSP portal administrator privileges] (https://mspbackups.com/AP/Administrators), kindly ensure that your S3 storage account has been added using the IAM Role (MBS wizard) or IAM Role (Manual, best practice) authentication type, not legacy access / secret key pair of the root AWS user.
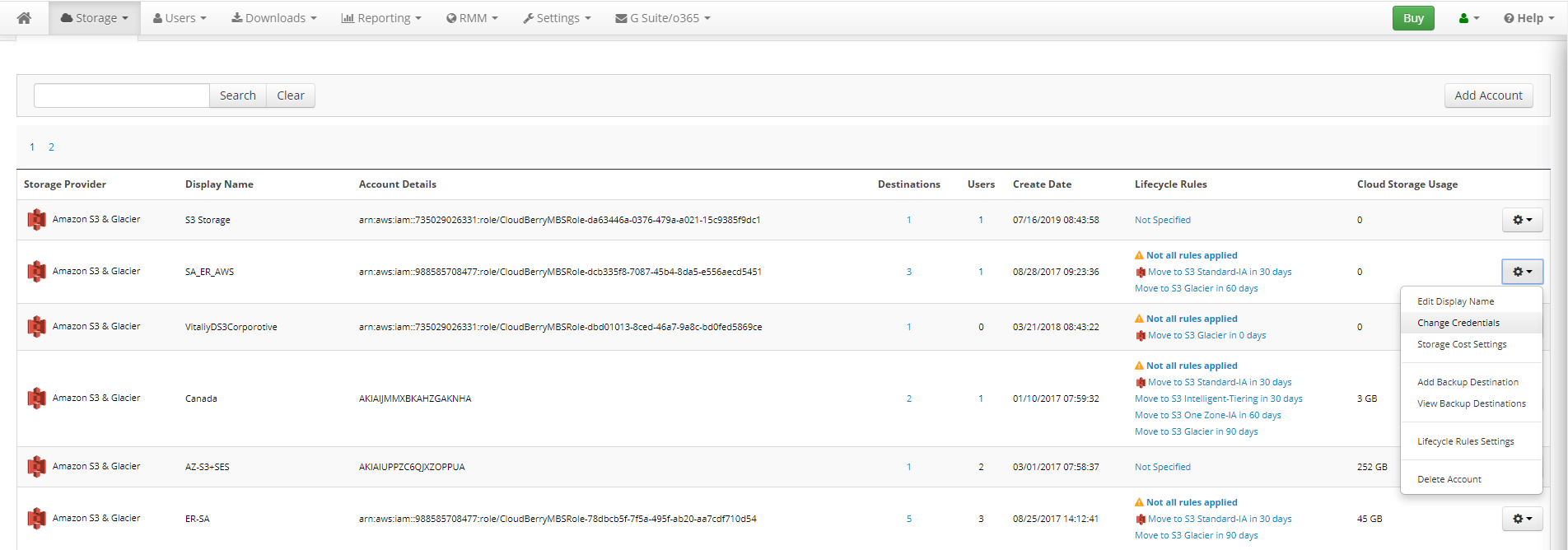
To ensure this:
- Open your [MSP portal] (https://mspbackups.com/AP/EditAccount.aspx);
- In the Storage menu, select Storage Accounts;
- Find the required account, then click the Gear button;
- Click Change credentials and check the authentication type.
2. Set up the vmimport IAM role again
In case all necessary IAM role / user permissions are set but the issue persists, try to set up the vmimport IAM role again:
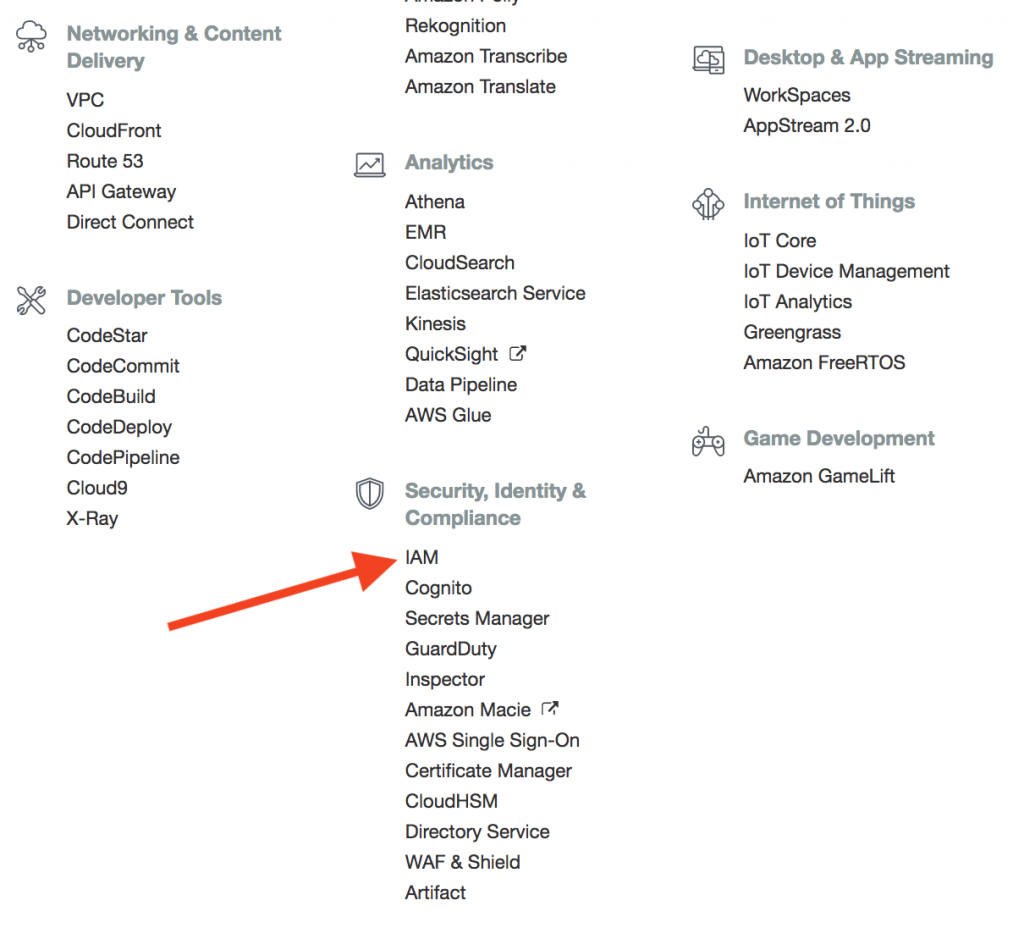
- Open your [Amazon Web Services management console] (console.aws.amazon.com);
- Log in using your Amazon root / user credentials;
- In Security, Identity & Compliance category, select IAM:
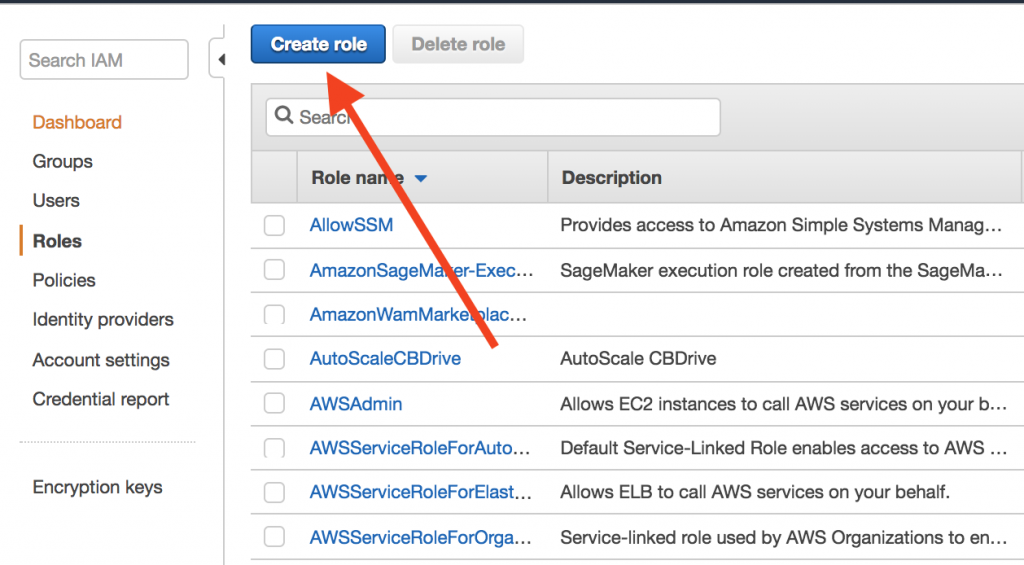
- Select Roles, then click Create role:
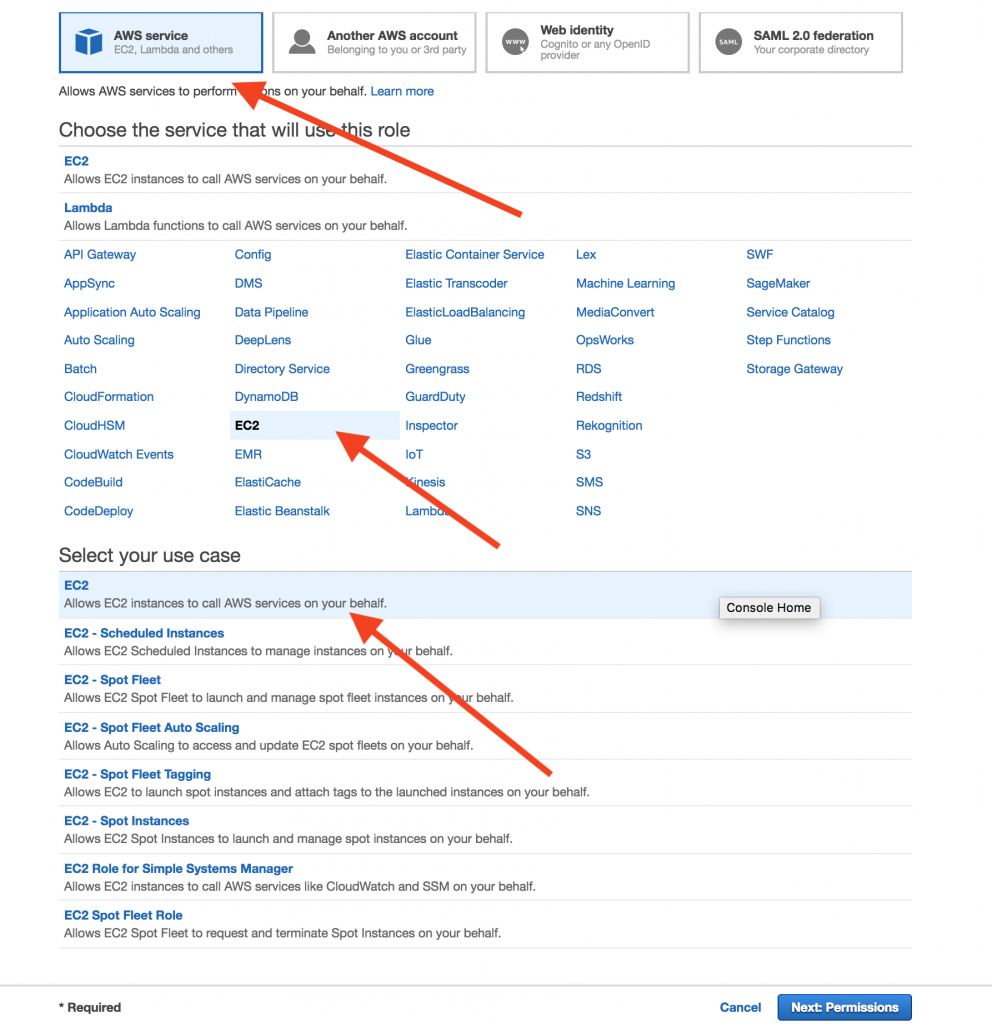
- Select the type of trusted entity (AWS service), then select the service for the role (EC2):
- Click Next: Review;
- Specify the name for the role (vmimport), then review the role's summary and click Create Role:
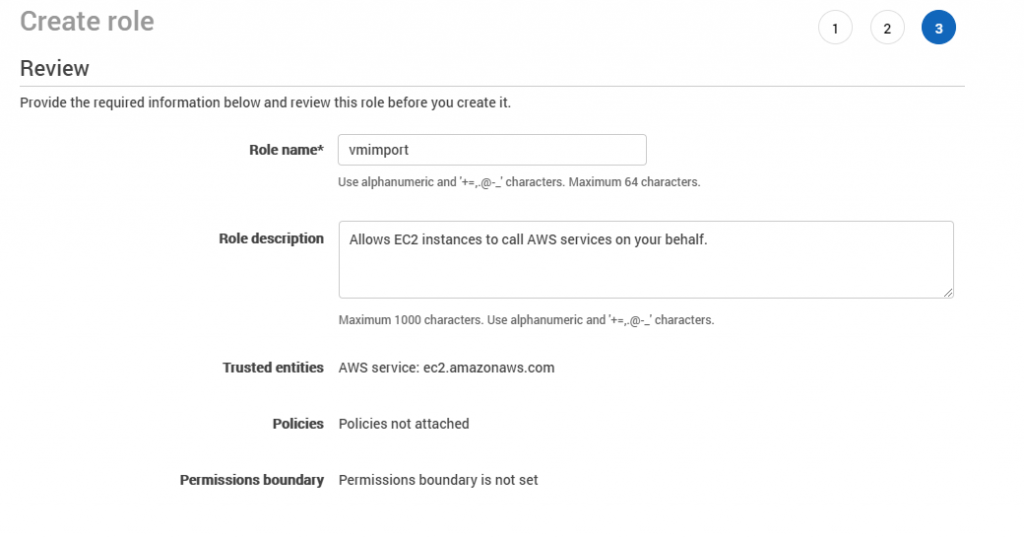
Make sure that the role's name is exactly that: vmimport
- Click on the created role to edit role policies:
- In the Permissions, click Add Inline Policy;
- Switch to the JSON policy editor, then insert the following policy:
{
"Version":"2012-10-17",
"Statement":[
{
"Effect":"Allow",
"Action":[
"s3:ListBucket",
"s3:GetBucketLocation"
],
"Resource":[
"arn:aws:s3:::{your bucket name}"
]
},
{
"Effect":"Allow",
"Action":[
"s3:GetObject"
],
"Resource":[
"arn:aws:s3:::{your bucket name}/*"
]
},
{
"Effect":"Allow",
"Action":[
"ec2:ModifySnapshotAttribute",
"ec2:CopySnapshot",
"ec2:RegisterImage",
"ec2:Describe*"
],
"Resource":"*"
}
]
}
Make sure that instead of "{your bucket name}" placeholder ("arn:aws:s3:::{your bucket name}") you have specified the name of the S3 bucket containing the image-level backup.
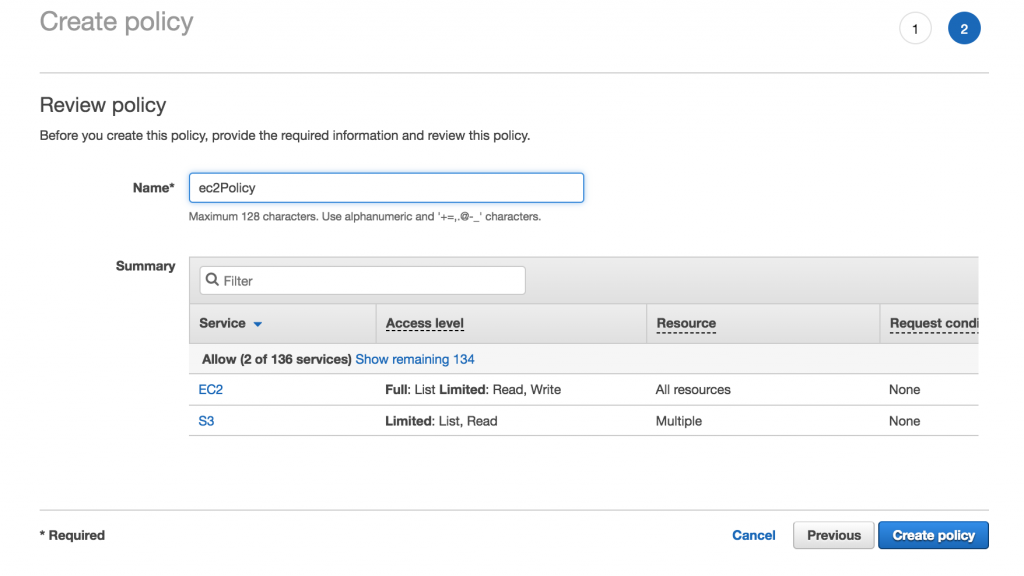
- Once all is set, review the created policy, specify the policy name, then click Create Policy:
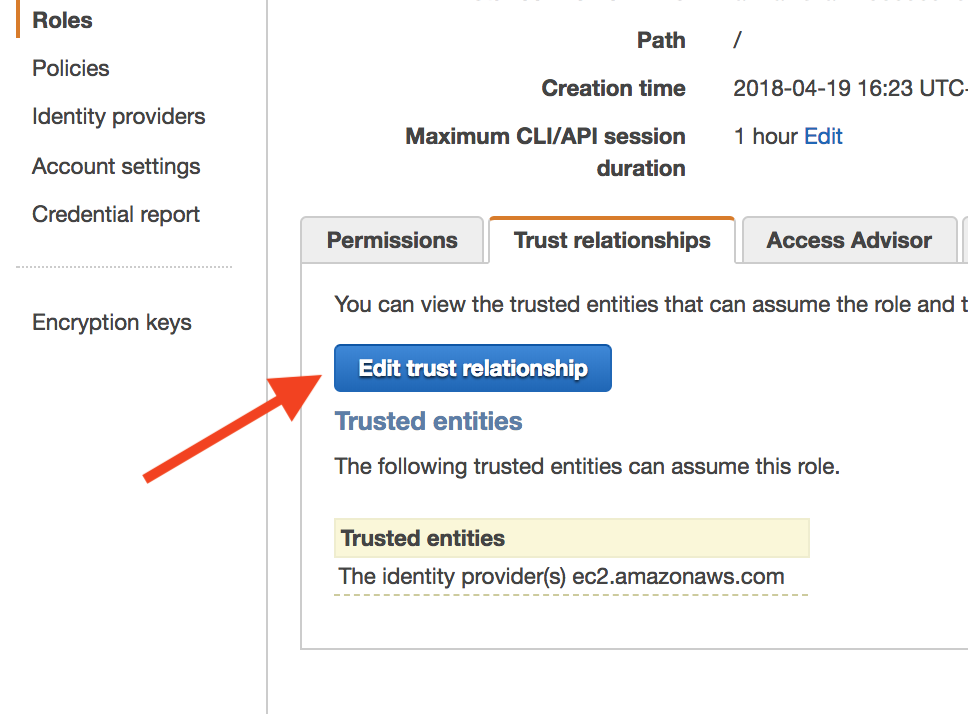
- Open the Trust Relationships section, then click Edit Trust Relationships:
- In the Policy Document editor, insert the following script:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Principal": {
"Service": "vmie.amazonaws.com"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": "vmimport"
}
}
}
]
}
- Once you are done, click Update Trust Policy.
3. Re-add AWS S3 storage account to your MSP portal through the "IAM role (MBS wizard)" option
In case the issue still persists despite the measures described above and you are granted with the [MSP portal administrator privileges] (https://mspbackups.com/AP/Administrators), please try to re-add your S3 storage account to the MSP portal again from scratch by using a brand new IAM user (that will in turn help to set up a proper IAM role).
To perform this:
- First, open your [AWS management console] (console.aws.amazon.com);
- Create a new IAM user with the following minimum of required permissions:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"iam:PutRolePolicy",
"iam:CreateRole",
"iam:GetRole",
"s3:ListAllMyBuckets"
],
"Resource": "*",
"Condition": {}
}
]
}
- Now open your [MSP portal] (https://mspbackups.com/AP/EditAccount.aspx) and proceed to the Storage Accounts tab;
- Add a new storage account and choose the "IAM role (MBS wizard)" authentication type in the opened menu;
- Specify your brand new IAM user credentials;
- Then follow the steps of the "Add Cloud Storage Wizard" in order to finish adding the storage account. The MBS wizard will ensure that a new storage account contains all the necessary roles, permissions, and policies related to the assigned IAM user and will also automatically create a properly set IAM role.
Reference materials
If you have any questions after reading this article, consider these materials for further reading: