Why It Is Not Enough To Make Your Bucket Public For Your MBS Users
One of the main priorities for MSP360 (CloudBerry) is our customers data security. We implementing different security mechanisms in our products and continuously trying to prevent data corruption, lost or compromising.
One of the available methods for our MBS (Managed Backup Service) is using IAM (Identity and Access Management) users with AWS (Amazon Web Services). In our kb post you can find how to set up the limited permissions under your AWS account and apply this permissions to your customers.
Why it’s not enough to grant full access to your S3 bucket? Let’s say, assign AmazonS3FullAccess and forget about it.
Provider shares his storage with end users though MBS. Meanwhile, end user doesn’t have secret key and access key for direct access to S3 bucket. How can end customer who uses his own credentials (login and password) for MBS backup agent request an access to provider’s S3 bucket? For such purposes in our policy for IAM users we add STS (Security Token Service).
The AWS STS is a web service that enables you to request temporary, limited-privilege credentials for AWS IAM users or for users that you (as a service provider) authenticate (federated users).
In our policy you can find the statement which is responsible for obtaining STS.
Here you are:
{
“Effect”: “Allow”,
“Action”: “sts:GetFederationToken”,
“Resource”: “*”,
“Condition”: {}
}
Here is the scheme how it works:
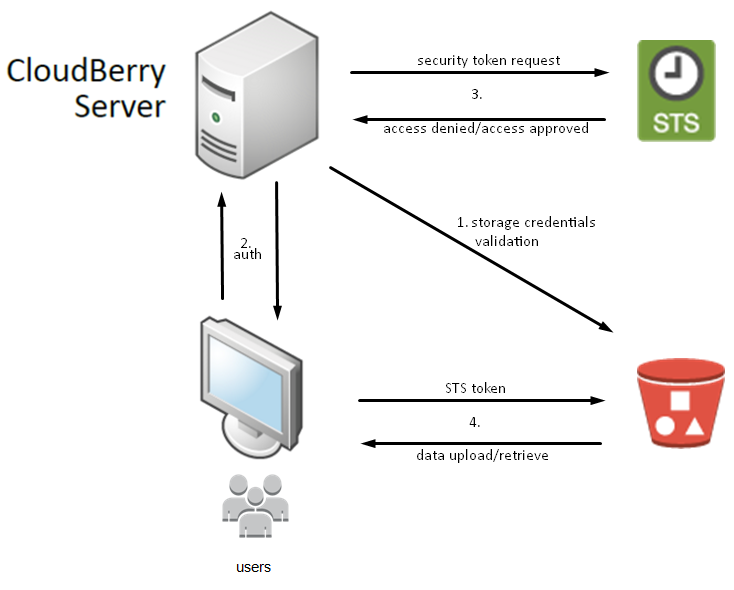
With MSP360 (CloudBerry) you can implement different security methods to protect your data and access to the storage. One of them is using IAM users with AWS.
Contact Us
- Tech questions
- Sales questions: sales@msp360.com