Ransomware Protection Recommendations
Ransomware has grown to be one of the most dangerous problems on the web. It appears as a form of malicious software which encrypts files on a computer or does it remotely.
This article covers the following topics:
What is Ransomware?
Ransomware is often spread through phishing emails that contain malicious attachments or through drive-by downloading. Drive-by downloading occurs when a user visits an infected website and then a ransomware trojan is downloaded and installed without the user’s knowledge.
Encoders, a malware species that encrypt files, are spread through similar methods and have also been spread through social media, such as web-based instant messaging applications, for example. Additionally, newer methods of ransomware infection have been observed. For example, vulnerable Web servers have been exploited as an entry point to gain access to an organization’s network.
Nowadays, if you are attacked with file-encrypting ransomware, criminals will brazenly announce they're holding your corporate data hostage until you pay a ransom in order to get it back.
It sounds simple, but it's efficient: latest statistics state that cybercriminals pocketed over $1 billion from ransomware attacks during 2016 alone as well as a Europol report describes ransomware as having "eclipsed" most other global cybercriminal threats in 2017.
Retention Policy off the Bench for Assistance
Try the retention policy best practices for ransomware protection.
Customize the retention policy that suits your requirements for ransomware protection.
- Edit the required backup plan.
- Follow the backup wizard to the Retention policy step.
- Customize the retention settings according to your preferences. Set the 'Keep backup for' value at least 5 weeks.
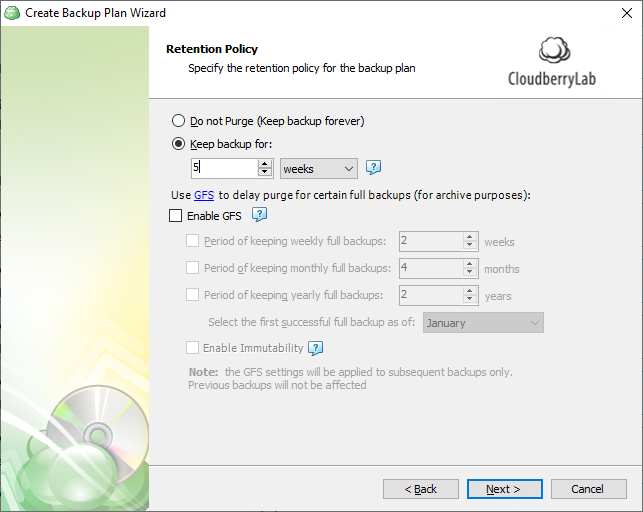
- As you finished configuring the retention policy, click Next, then follow the backup wizard to its end to save the backup plan configuration.
Legacy Backup Format
It is recommended to set a purge delay of 30 days or more to ensure any ransomware infection that renames files does not cause your old (good) backups to be removed from backup storage. With this setting, any locally deleted files will remain in backup storage for the specified number of days so you have the time to find out the ransomware attack that unfortunately occurred and your backups are ready to restore as the ransomware is neutralized.
Customize the retention policy that suits your requirements for ransomware protection.
- Edit the required backup plan.
- Follow the backup wizard to the Retention policy step.
- Customize the retention settings according to your preferences.
- Specify custom retention policy for backup plan option allows you to create a customized retention policy that helps you to keep your files safe from ransomware attacks. Select it to activate the retention policy settings
- Delete versions older than option allows you to customize the periods of your file version deletion. Select the appropriate check box to make the detailed settings available. Use the spin boxes to specify the period of keeping your file versions for the required period of time to secure them from ransomware attacks
- Specify the counting mode by selecting the corresponding item (modification date or backup date) from the drop-down menu to the right. It is recommended to use the backup date in order to build protection against ransomware
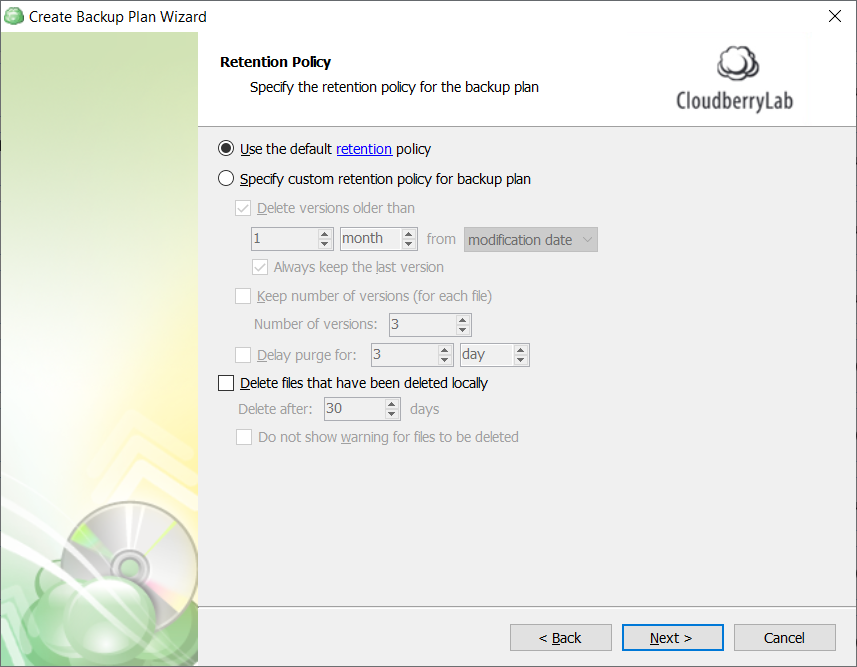
- Keep number of versions (for each file) option enables you to specify the number of file versions that are kept in your backup plan. This secures your files in case they are encoded by ransomware, as you can easily restore the clean file version. It is recommended to keep at least 3 versions. You can specify the number of versions kept using the Number of versions spin box
- The Delay purge for option allows you to customize the period within which your file versions are not purged from the backup. Select the corresponding check box, then specify the purge delay period. The recommended value for this setting is 2 weeks
- The Delete files that have been deleted locally option allows you to manage the deletion of files in your backup storage that are deleted locally. To secure your backup against ransomware attacks, it is recommended that you keep this check box clear
- Do not show warning for files to be deleted is an option that allows you to avoid receiving warnings about the deletion of files stored locally. In the context of ransomware protection settings, it is not recommended to keep this check box selected
- As you finished configuring the retention policy, click Next, then follow the backup wizard to its end to save the backup plan configuration.